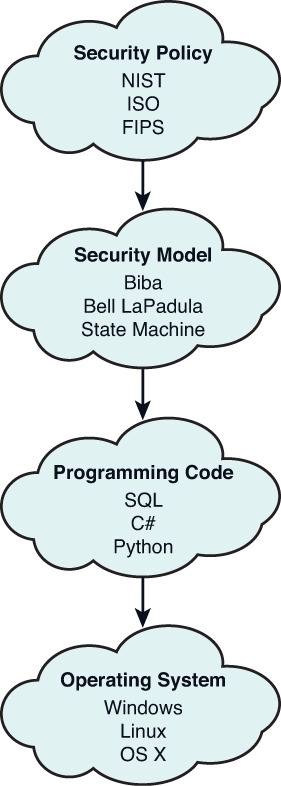
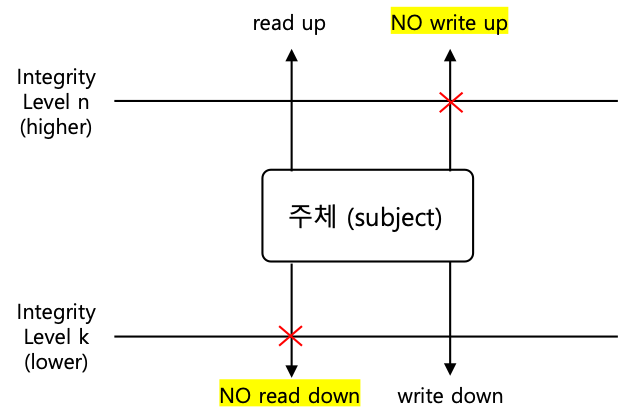
Two Laws of Biba Model The satisfaction of both Biba laws, prevents the... | Download Scientific Diagram
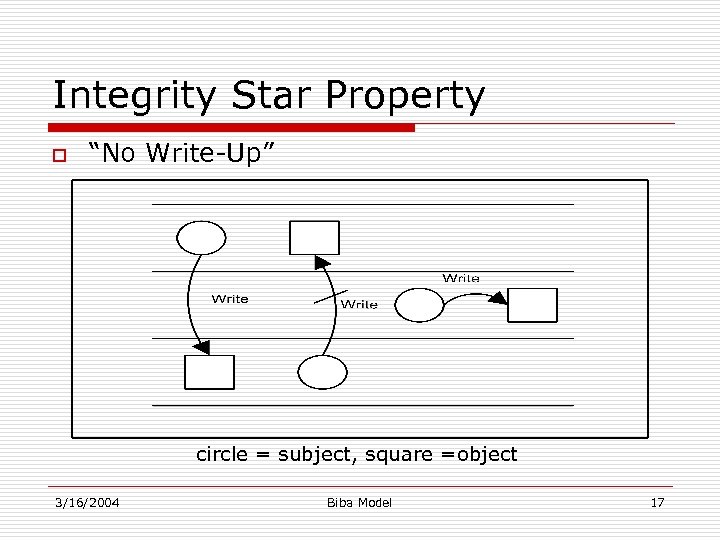
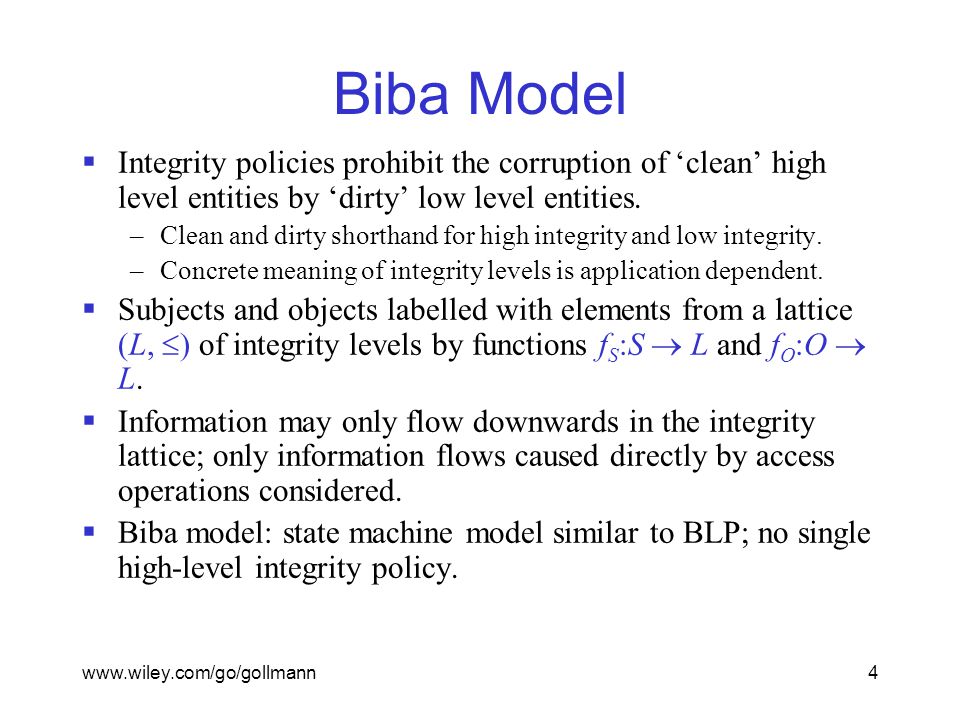
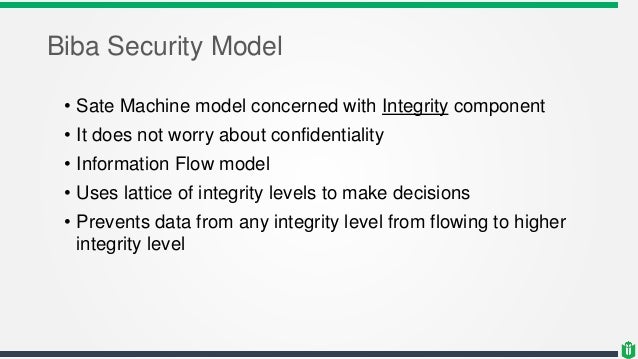
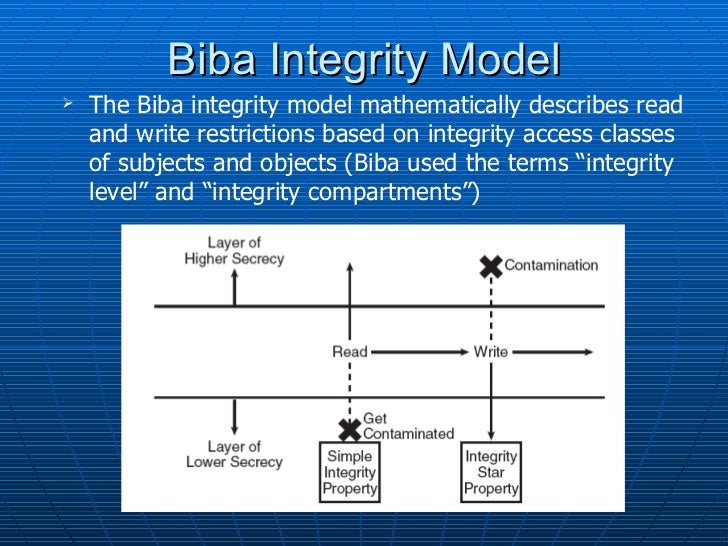
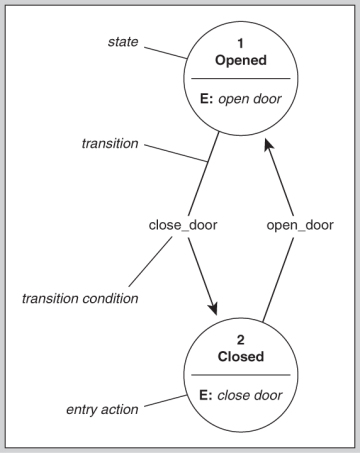
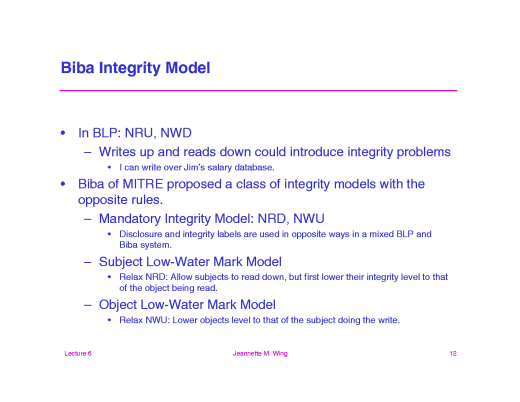
Integrity Models Biba Integrity Model (1977) Biba Model – ”no read down” Biba Model – ”no write up” Biba Model – i

Two Laws of Biba Model The satisfaction of both Biba laws, prevents the... | Download Scientific Diagram